
There is a persistent belief among the SME business community that cyber security threats target mainly larger corporations. While this may have been true many years ago, it’s no longer the case today. In 2022 for example, there was a 38% rise in cyber-attacks targeting SMEs, with smaller enterprises often viewed as weak links in a supply chain. Cybercriminals often use these ‘weak links’ to prey on more lucrative targets, with almost one fifth of attacks targeting large global firms thought to exploit an SME in the supply chain as what you might term an ‘attack intermediary.’
Recent years have seen a sharp rise in both the prevalence of cyber threats and their efficiency. The Covid pandemic, which saw millions of us working from home, presented boundless opportunities for cyber criminals, with many businesses struggling to implement remote working in a secure, considered way. Technological developments, such as the development and increased availability of AI, have seen the criminal community adopt new technologies to undertake more effective, damaging attack campaigns. Additionally, the rise in digital activity more generally is thought to be fuelling the longstanding rise in cybercrime, with criminals drawn online by potentially greater rewards.
Despite increased awareness, many organisations are failing to grasp the gravity of the situation, with only 23% of businesses having a formalised cyber security strategy in place according to the 2022 Cyber Security Breaches Survey. Poor, limited or non-existent cyber threat mitigations are particularly common among SMEs, with many citing limited budgets and lack of staff capacity as reasons for their lack of preparedness.
In order to defend your business, it’s vital to have a multi-layered security strategy that seeks to mitigate cyber threats wherever they present. This means using firewalls to defend your network from untrusted corners of the web, deploying endpoint detection and response to monitor for threats and take remedial action. Also establishing email security tools to mitigate the risks posed by email-borne malware and phishing attempts. These controls should be used alongside organisational measures, such as staff security awareness training and the publishing of information security policies, to ensure that your employees represent a defensive asset rather than a liability. Lastly, this strategy should also consider a key cyber security vulnerability that often gets overlooked: Microsoft 365.
Data Security in Microsoft 365 – Shared Responsibility
Organisations that use Microsoft 365 often believe it’s secure by default. After all, a cloud-hosted service provided by a global giant like Microsoft’s got to be secure, right? Well, it’s not that simple. While Microsoft invests over $1 billion on cloud security each year, this focuses mainly on the integrity and resilience of its platforms and services. You, as a business owner, bear a sizable chunk of responsibility when it comes to protecting the data you store and process in the Microsoft ecosystem.
Microsoft’s responsibilities
Microsoft is responsible for maintaining the uptime of its services and the defence of its data centres against physical threats and brute-force cyber-attacks. Geo-redundancy and replication are provided to protect data in the event that one location becomes inoperable, and a limited degree of data retention is offered by default; useful for restoring mistakenly deleted files.
Your Responsibilities
You are responsible for implementing controls that ensure only authorised, authenticated individuals are able to access your data. It’s also your job to apply appropriate controls to the information you hold to prevent accidental or malicious editing, deletion or theft. This means diligently applying the user access controls that all Microsoft services come equipped with, and extending user privileges to employees on an as-needed basis in order to minimise risk. Preventing the intentional or accidental introduction of malware is also a responsibility that lies with your business, as is implementing a data backup solution that satisfies your retention needs and operates in line with your compliance requirements.
In summary, while Microsoft assumes responsibility for maintaining the integrity of its services, the protection of any data you choose to host in Microsoft 365 remains your business’s responsibility.
How to Secure Your Microsoft 365 Accounts – A Brief Guide
There are a range of steps you can take to strengthen the security of your Microsoft 365 accounts. For optimal protection it’s best to take an approach that combines 365’s in-built security features, supplementary external measures, and a range of organisational practices that aid your data protection objectives.
Let’s take a look at some of the key ways you can make your Microsoft 365 accounts more secure. Depending on the Microsoft 365 subscription you have, many of these could be immediately actionable.
Threat Policies
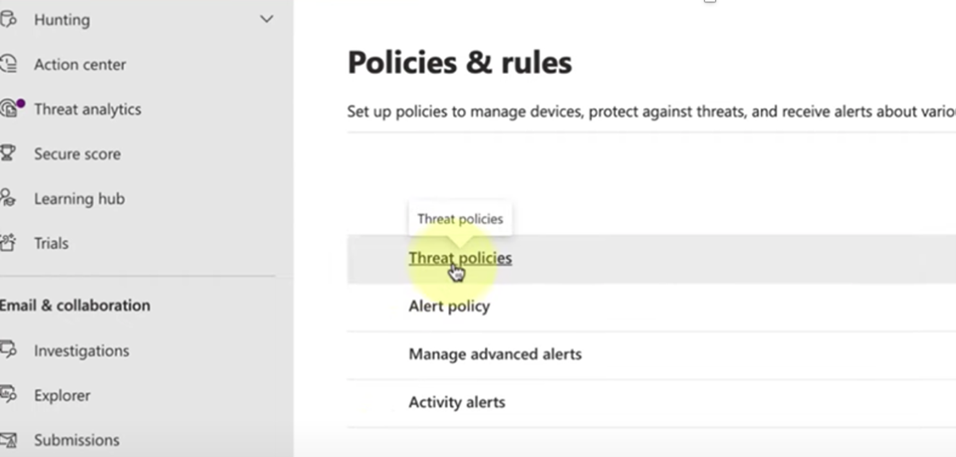
Microsoft 365 features a number of pre-set email protections designed to counter spam, phishing attacks and email-borne malware. These should be already activated, but to check that they are, and to reconfigure for maximum effect, navigate to the ‘security centre’ in your 365 admin centre, and locate threat policies on the ‘policies and rules’ page.
Role-based access control (RBAC)
Role-based access control refers to the practice of extending user privileges or resource access rights on the basis of job role. To optimise your business’s security posture it’s advisable to restrict the access user accounts are afforded on a strictly as-necessary basis, and to minimise the number of accounts hosting extensive management privileges.
In Microsoft 365, the highest level of user privilege is that of the ‘Global Admin:’ typically the person who initially purchased the subscription. This account features the widest management privileges, including the ability to add and remove users, manage domains, reset passwords, and extend/withdraw admin privileges to/from other users. With such extensive privileges, such an account could be used to disastrous effect in the wrong hands. It’s therefore vital to operate as few Global Admin accounts as possible to reduce security risk – ideally no more than 2 or 3.
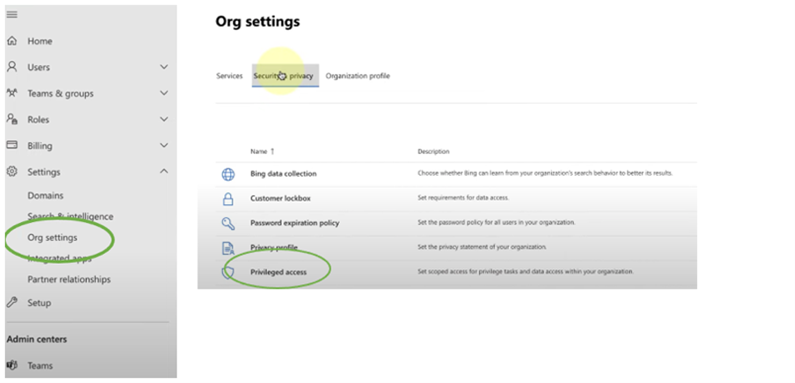
Fortunately, granting privileges to users in Microsoft 365 doesn’t have to be on an all-or-nothing basis. Through the MS 365 Admin centre you can assign granular privileges on a time-limited basis to allow users to perform certain tasks without subjecting your system to excessive risk. To do this, navigate to ‘Org settings,’ click on the ‘Security and privacy’ tab and select ‘Privileged access’ as depicted below.
Multi-factor Authentication
Requiring the submission of 2 or more items of identifying information, multi-factor authentication (or MFA for short) provides more secure authentication than traditional email/password combinations. The additional identifying information required by multi-factor authentication is typically something only the authorised end-user could feasibly provide, and could include the likes of biometric identifiers (finger prints, face scans etc) or a pin or code sent to a user-registered device or account.
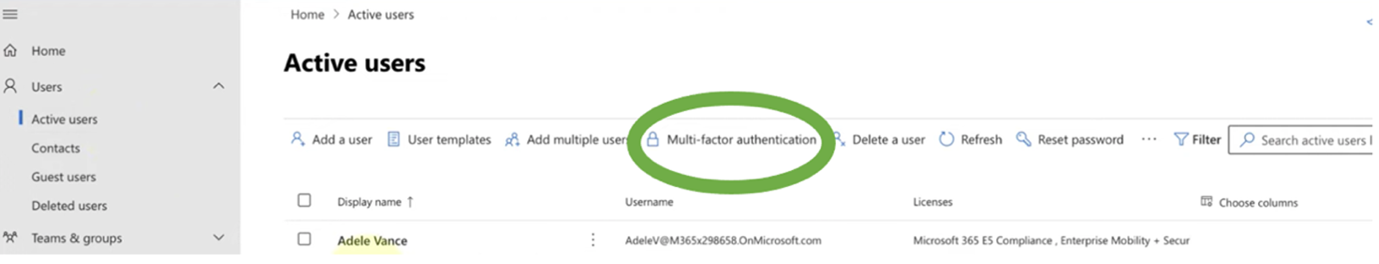
Multi-factor authentication can be enforced within the Microsoft 365 Admin centre, through the ‘Users’ side menu as shown below.
There are a number of verification options available, including the ability to have authentication codes sent by text, or called through to registered phone number. The recommended verification option, however, is using the Microsoft Authenticator Mobile app. Once registered to a user’s account, this app presents push notifications to the user’s phone upon each sign-in attempt, providing simple, secure, one-click verification.
Secure Score
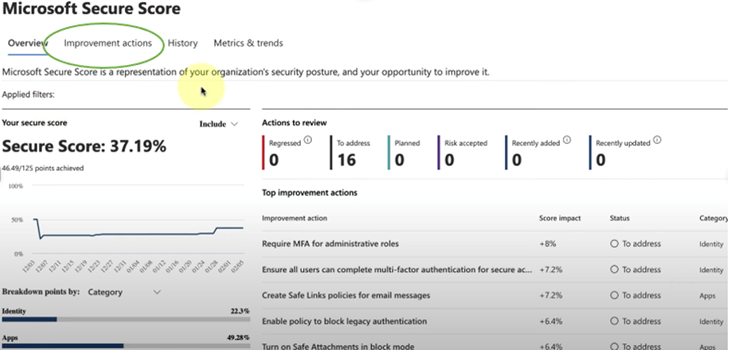
Among the most useful Microsoft 365 security tools is the intuitive and helpful ‘Secure Score’ feature. Found within the MS 365 admin centre, this tool provides a dashboard-style overview of organisational security posture, as well as a list of recommended improvement actions. ‘Secure score’ refers to the percentage score assessed by the system, which combines a number of separate scores calculated against various individual security categories, including identities, data, devices, apps and infrastructure. By ordering prescribed improvement actions based on likely impact, Secure score makes it quick and easy to review operational security and quickly make changes which have a meaningful impact on security posture.
Mobile Device Management
If your employees work remotely, even on a partial basis, it’s important to ensure their remote devices are properly maintained and configured in line with security best practice. You can of course require that staff submit their remote work devices for a periodic audit to ensure the required standard is being met, but it’s far easier and less invasive to use a mobile device management solution.
Microsoft 365 users may want to consider Microsoft Intune for implementing mobile device management. Featuring integration with Azure Active Directory, and forming part of Microsoft’s Security and Mobility Suite, Microsoft Intune provides cloud-based remote endpoint governance, covering apps, identities and devices: perfect for securing remote Microsoft 365 users.
Data Loss Prevention Policies (DLP)
Configurable from within Microsoft Purview, data loss prevention policies enforce controls which aim to prevent the loss, deletion or misuse of sensitive information types.
DLP can perform environment-wide content analysis to detect sensitive information types across a wide range of platforms and devices, including Outlook, Exchange, SharePoint, Microsoft Teams, Word, Excel, PowerPoint as well as macOS, Windows 10 and Windows 11 endpoints. Should the system detect the misuse or mishandling of information deemed sensitive, a number of protective actions will be triggered according to user-configured data loss prevention policies. These include:
- Blocking sensitive information from appearing in Teams chats.
- Automated pop-ups warning the user that they’re about to share sensitive information inappropriately.
- The forcible blocking of unauthorised sharing.
- The forcible blocking of unauthorised sharing with an override option.
- The removal of sensitive information to a quarantine location.
Back up your Microsoft 365 accounts using a third-party service
Microsoft 365 contains several features and characteristics that some users mistake for data backup functionality. One of these is geo-redundancy, which sees user data mirrored across multiple, geographically dispersed sites to aid service resilience. Another is the existence of data retention policies, which provide some protection against the permanent deletion of Microsoft 365 data. However, 365’s document retention capabilities have their limitations when compared to dedicated backup services:
- While Microsoft 365’s retention policies apply to emails, folders and files, other items such as calendar entries in Exchange, chat attachments in Teams and settings such as access permissions, and group data fall out of scope.
- When you choose to delete an item the retention policy applied is overruled. The standard retention time applicable to each platform is then applied before hard deletion is performed. In SharePoint this time is only 93 days, beyond which point data becomes unrecoverable.
- Geo-redundancy doesn’t mean backup. Although it sounds like your data is being copied to multiple locations in a similar fashion to a data backup, the purpose of geo-redundancy is to ensure service continuity: not as a data safeguard.
For added protection, consider operating a dedicated Microsoft 365 backup that offers encryption, customisable backup scheduling, point-in-time restoration capabilities and unlimited backup storage.
Extended Threat Detection and Response (XDR)
Extended threat detection and response platforms are security solutions that apply detection, analysis and response capabilities environment-wide, offering protection to clouds, networks, apps, devices and identities.
Microsoft Defender is one such solution, offering cloud-native protection that works in perfect harmony with Microsoft’s cloud platforms. It combines traditional anti-virus protections (the ability to scan files, attachments and downloads for the presence of malware) with next-gen, AI-driven capabilities in the form of behavioural analytics in order to detect anomalous activity that could signal an emerging threat. Encompassing multiple protection technologies into an intuitive, centralised platform, Microsoft Defender is a superlative security tool for organisations serious about cyber security.
Conclusion
While Microsoft’s cyber security credentials are strong, poor management of your Microsoft 365 accounts could leave your data vulnerable.
With the likes of Azure Active Directory and Microsoft Intune, Microsoft makes it easy to manage access and identities across your accounts. Unified security solutions like Defender provide wide-ranging threat detection, analysis and remediation capabilities, extending security protection to all employees wherever they’re working from. And with in-built security features like multi-factor authentication, email filtering and Secure score, Microsoft 365 provides many ways to improve the security of your accounts. All that’s required of you is a willingness to explore the security features and platforms on offer, and put them to use.
We are Blucando, the Southeast’s Premier IT Support Provider
From our base in Farnborough, Hampshire; we are a full-suite IT provider offering technology support, management and consultancy to businesses across Surrey, Hampshire, London and the wider southeast region. We pride ourselves on delivering robust, dependable IT systems our clients can rely on, coupled with strategic guidance that helps unlock business potential through technology. Get in touch today to find out how Blucando could help level up your business through technology.

